Bulletproof privacy in one click
Discover the world's #1 privacy solution




Coming soon

Coming soon

Coming soon


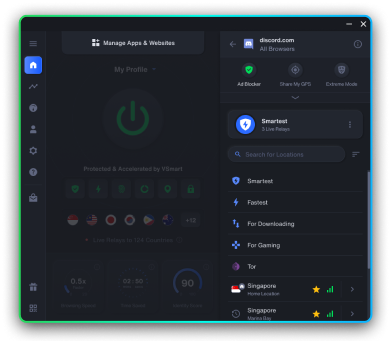

Hoody Blog is written by privacy experts with advanced technical knowledge. Get unique and uncensored news, insights and everything related to Privacy.





Chapter 14: IoT Hacks

Dive into the unsettling world of government-controlled GPS tracking!

Trash Talk: How your garbage can be exploited by hackers, law enforcement, and government agencies

It’s time to uncover how government surveillance gets personal.

Lifting the lid on the internet's most invasive tracking method: Browser fingerprinting.

The silent menace shaking the core of IT security

DuckDuckGo vs. Startpage: Which search engine reigns supreme for your online privacy?

Forget the tin foil hat myths, discover the very real and growing threat to your privacy: Laser Listening Systems

Think VPNs give you online anonymity? Think again.

Find out how governments are using satellites to spy on their own citizens.

Explore how your device's unique 'canvas fingerprint' is shaping the internet you see and how you can take back your privacy.

Discover the various ways that countries all over the world spy on citizens without any specific mandate.

Ever wondered how your data gets harvested online? We unmask the world of web scraping.

Hackers aren't the only ones who use botnets...

The Marketer's Hidden Weapon: How device fingerprinting knows you better than you might think...

Chapter 5: A history lesson and future look at how the government is destroying encryption.

Are you unknowingly revealing your digital identity? Learn how browser extensions can make you stand out in the crowd!

Chapter 4 - Social Media Analysis. Find out how your social media sharing is feeding right into government mass surveillance machine.

Virtual Machines: Not just for techies! Discover how VMs can safeguard your online privacy.

Meta and Facebook phishing scams take a dark turn. Learn about the latest tricks being used, and the damage they cause.

Unstoppable domains are popular with the tech-savvy. But are these crypto domains the real deal?

Discover how SOCKS5 proxies can safeguard your online identity and why they're a game-changer for privacy enthusiasts.

Get ready to explore the truth, one chapter at a time.

Warning: Getting caught out by one of these Instagram phishing scams could cost you more than just your paycheck!

Find out how social media platforms collect your data and learn 10 quick hacks to protect your privacy.

Hacked YouTube account? Don't let years of work, thousands of followers go down the drain. Here's what to do.

Are you so sick of ISP throttling that you would do anything to stop it? How about becoming your own ISP with a WISP?!

Want evidence that device and browser fingerprinting are dangerous? Hold onto your hats, we're getting technical.

Get the lo-down on data brokers. What are they, how do they operate, and how to protect your valuable personal data and online privacy.

The UK government wanted real identities as online handles, and people rebelled. Anonymous Twitter lives on!

In a post-Roe America, your every move online could be used against you.

Discover the world's worst internet freedom offenders - Is your country on the list?

Third party browser cookies in Chrome are being banned. But what about Browser fingerprinting

Do you know the difference between a VPN and a proxy? Which is faster, more secure, or better for streaming?

Keep your financial secrets safe! Learn about anonymous payments and how they can shield you from identity theft and unwanted surveillance.

Big tech censorship has nothing to do with conspiracy theory. It's about global policies that hurt millions of people.

Has Elon ruffled your blue feathers? Learn how to deactivate your Twitter account and take your Tweets with you.

Worried about Google spying? You let them control your E-mail, monitor your videos, and you invite them into your home

Staying connected and sharing life has a price: privacy. Find out which social media apps are the most data-hungry and what you can do about it.

Today is absolutely the day to delete your Reddit account! We'll explain why, and give you simple instructions on how.

Type in a bunch of numbers, get a domain name? Why is that useful?! Reverse DNS is more important than you think.

Meta's controversial 'Pay for Your Rights' model: What's at stake for EU users?

Learn about how one of the most popular Twitch ad blockers was leaking IDs to Russia, and the alternatives you can use.

Don't game in the dark! 10 must-know tips to protect your privacy online

Looking for the best torrent site? Read our qBittorrent review to see if it makes the grade.

Minority Report or reality? The dangers of preemptive surveillance in Sweden

Browser fingerprinting is like internet tracking on crack. It's highly invasive and impossible to block even with a VPN or Tor.

Looking for new reading material? Unleash your inner privacy pro with this reading list on online security!
Find out which encrypted chat app is best at stopping surveillance and safeguarding your privacy.

Privacy Under Attack: How Mass Surveillance Threatens Your Freedom

Do you know what information your IP address reveals? It could be enough to put your privacy at risk.

Have you ever gotten the 'DNS server not responding' message and wondered why? Learn the common reasons and fixes.

Whether you're a company or an individual, these processes need to be followed in order to prevent data breaches.

The first days after getting hacked can be life or death for a company. Learn the steps to take if you want to survive.
Discover the world's #1 privacy solution
Coming soon
Coming soon
Coming soon

