
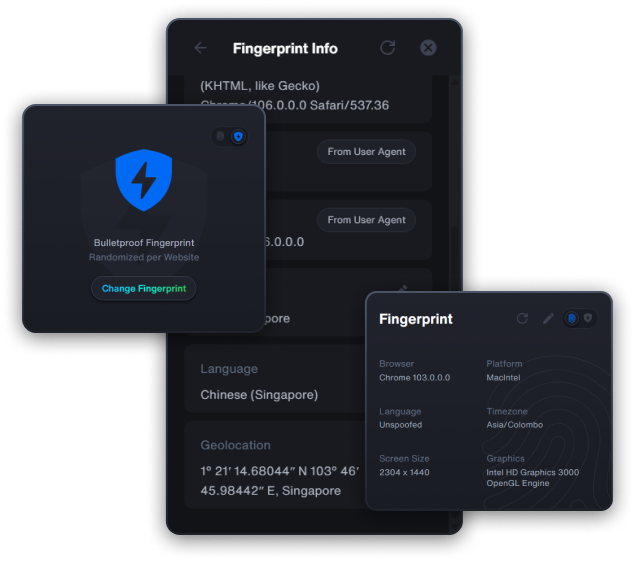
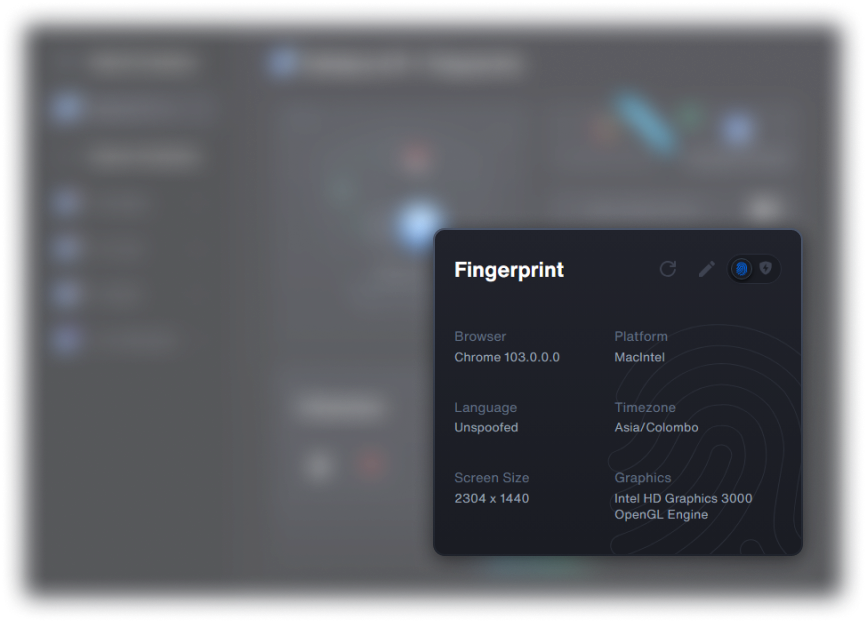
Even with a VPN, websites collect data about your browser settings, hardware, behavior & patterns, to create a unique identifier known as "fingerprint", allowing tracking across sites without cookies.
Generate a unique browser profile for each site, making it nearly impossible for websites to correlate your activities.
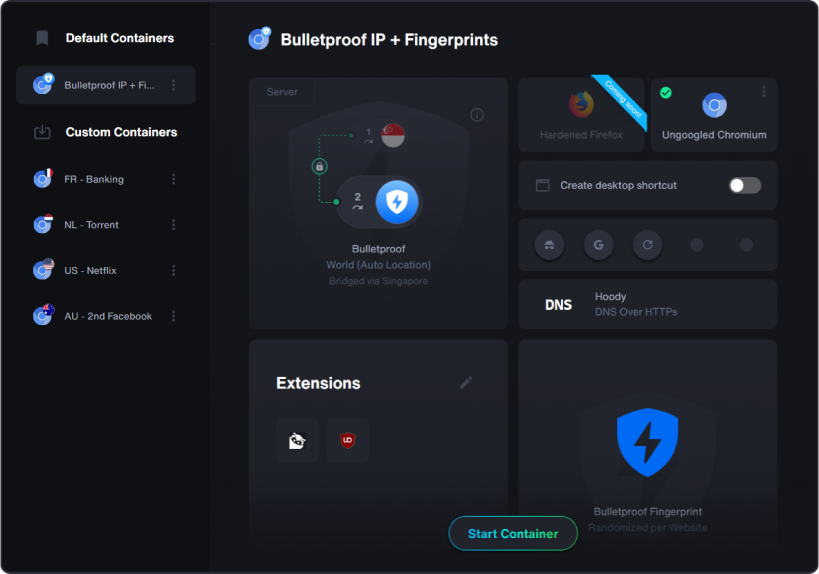
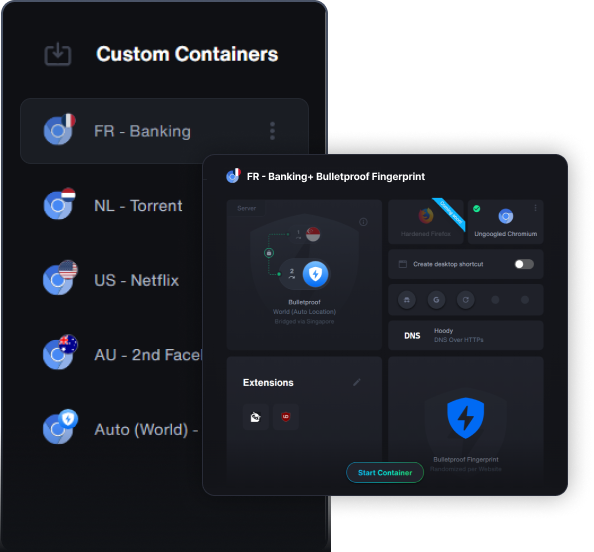
Each container supports unique, sticky fingerprints that you can manually adjust, allowing you to have a consistent profile for specific browsing tasks.
Launch unlimited Bulletproof isolated browsers.
Containers are essential for privacy, as most of the trackers collect your data through browser tracking. VPNs don't protect against browser and device fingerprinting but containerized browsing does.








Randomize your exit IP for each request, also available by Regions for best latency & speed.
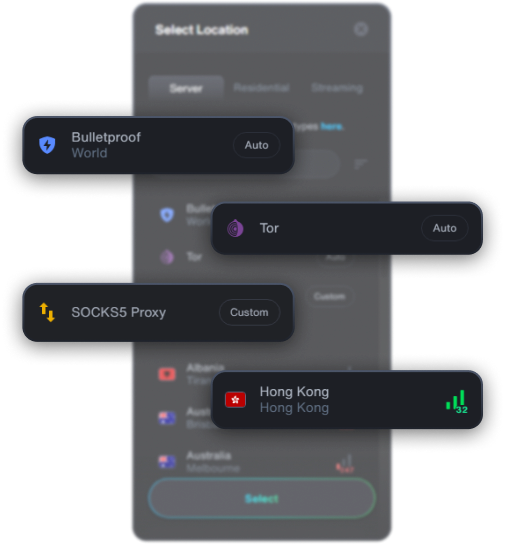
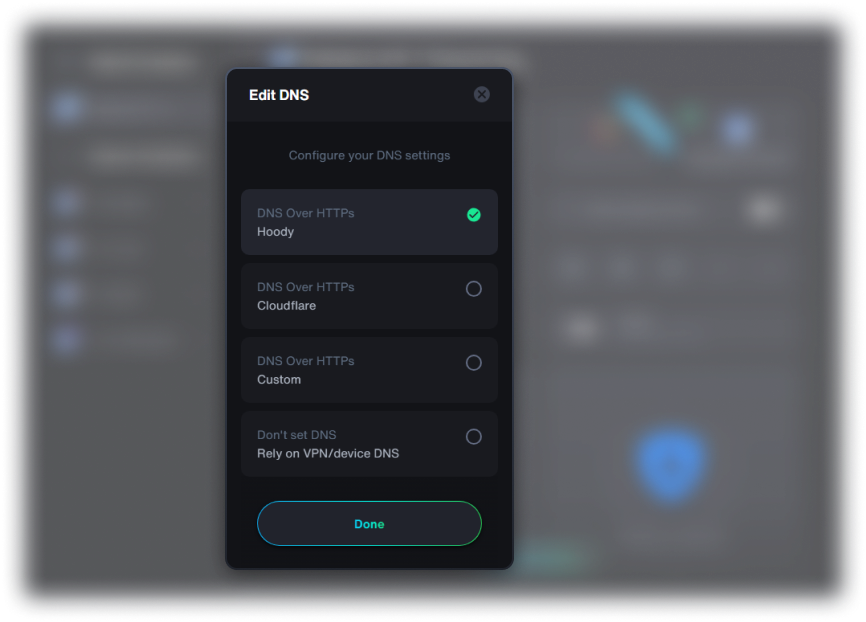
Use your own SOCKS5 proxy (compatible with credentials) for specific containers.
Route container's traffic through Tor for enhanced anonymity, with your exit IP being a Tor node.
Disable VPN protection for specific containers, allowing them to use your real IP address.
Assign aliases, icons, and settings to each container for easy identification and quick access of your Bulletproof browser.
Launch Bulletproof and custom browsing containers effortlessly from the systray in the bottom right of your OS.



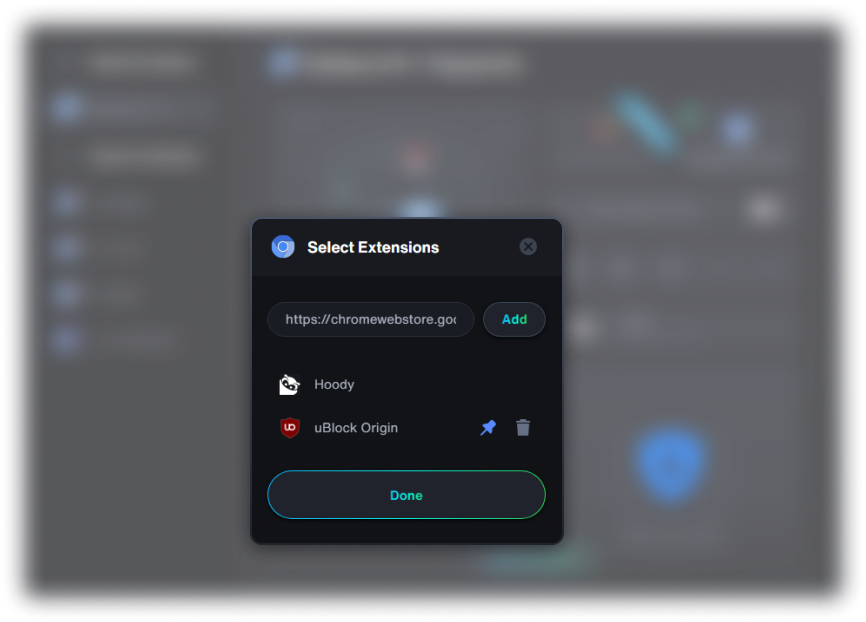
Customize containers with your favorite extensions. Input Chrome Store URLs and have them loaded before even starting the container.
Your unique Hoody Key is a cryptographic secret known only to you. We only store a double-hashed version of it, we have no way to know what a user is doing in our network.
ZNLNT - F42E - HYTI - L6SDE
Payments through any gateway, even non-anonymous ones like PayPal, are completely disassociated from your account, providing absolute privacy.
See Pricing