Bulletproof privacy in one click
Discover the world's #1 privacy solution




Coming soon

Coming soon

Coming soon



The Internet of Things (IoT) is a rapidly growing network of interconnected devices designed to make our lives easier. From smart home appliances to wearable technology, IoT devices have become an integral part of our everyday lives. However, Internet of Thing privacy is a growing concern. These devices collect and share a vast amount of user data presenting a whole host of privacy and security issues.
With data breaches and cyber attacks a common occurrence, users are becoming increasingly aware of the risks associated with IoT devices. We explore the growing number of Internet of Things privacy issues, the personal information that is at stake, and how users can protect themselves in this increasingly connected world.
The Internet of Things (IoT) refers to a network of interconnected physical devices. These devices or “things” are fitted with special technology and sensors capable of collecting and exchanging data with other devices or systems without human intervention.
IoT devices range from the mundane to the extraordinary. For instance, smart home systems allow homeowners to remotely control the temperature of their homes using their smartphones. Smart locks give the ability to lock and unlock doors remotely, providing homeowners with greater security and peace of mind. There are smart fridges, hoovers, plugs, cameras, laundry machines, doorbells, and many more “things” all controllable via the internet.
But it's more than your home appliances. IoT technology is also being used to improve healthcare. ECG and blood pressure monitors are now available as wearable devices that collect data that can be shared with healthcare professionals, allowing for more personalized and proactive healthcare. Fitness trackers such as Fitbit and Apple Watch monitor a person's heart rate, activity levels, and sleep patterns, providing valuable insights into overall health.
Smart cities are another example of IoT in action. Cities around the world are using sensors to monitor traffic flow, air quality, and even noise pollution. The data can be used to improve city planning, optimize energy usage, and reduce carbon emissions.
By the end of 2023, experts expect there to be more than 15 billion connected IoT devices, 20 billion by 2025, and 30 billion by 2030.
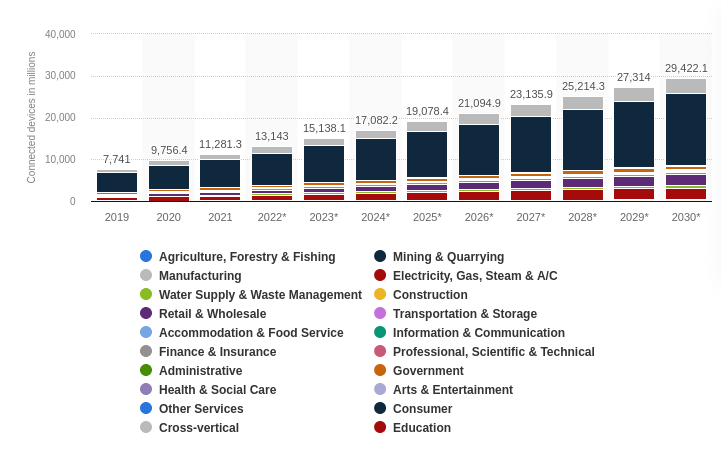 Image source: Statista
Image source: Statista
There's no denying, IoT technology has revolutionized the way we interact with our environment, providing us with a wealth of information and unprecedented control over our surroundings.
But at what cost?
Internet of Things privacy and security risks
The widespread adoption of IoT devices may have made life easier, but convenience comes with a significant side order of privacy and security risks.
These devices collect and transmit a considerable amount of information, some of it sensitive and most of it personal. They are an easily accessible treasure trove of information making them an attractive target for hackers and cybercriminals.
Below we mention just a few of the Internet of Thing privacy and security issues you should be aware of.
IoT devices lack security features
Most IoT devices lack basic security features, such as strong authentication and encryption protocols. This makes them especially susceptible to hacking which can result in the theft of sensitive data, give remote access to devices and networks, or even cause physical harm.
Until recently, the IoT industry had been fairly unregulated, with little-to-no security standards for devices. This led to a wide range of security vulnerabilities as IoT manufacturers prioritized functionality over security.
A single compromised device can weaken an entire network
IoT devices are often part of a larger ecosystem of interconnected devices. Just one compromised device can provide an entry point for hackers to gain access to an entire network, putting all connected devices at risk.
Limited computing power means limited security
Many IoT devices are small, lightweight devices that have limited computing power. This makes it difficult to implement sophisticated security measures. Neither are they built with security in mind which leaves devices vulnerable to attack.
Multiple third-party services
IoT devices may be small but they are quite complex in their design in the way that they are made up of many elements. Full functionality often requires integration with external third-party software.
The IoT manufacturer cannot always be certain that these third-party components are secure. The security protocols, if there are any, are often weak and this can compromise the security of the entire IoT device.
Additionally, with so many third-party services involved, controlling and securing the data collected also becomes a security issue.
What type of data do IoT devices collect?
Different types of IoT devices collect different types of data for different reasons. Depending on the type of device, the data might help improve user experience or allow the user to make better decisions about their own environment or their own health. Data can provide valuable insights to a business or to city planners allowing them to make better, more informed decisions.
We've picked five of the most common household IoT devices and looked into the type of data they collect. Note that the data collected may be more or less than is stated here depending on the device brand. You should always check the company's privacy policy carefully.
Doorbells
A “smart” doorbell is usually a three-in-one device comprised of a doorbell, camera, and microphone. This smart doorbell is connected to the WiFi and an app that allows the homeowner to see, hear, and record who is at the door.
But these devices collect an awful lot of data beyond video and audio.
Firstly, they collect the user's name, address, telephone number, payment details, and social media profiles (if they link their accounts). They also collect IP addresses, WiFi details such as signal strength, and any technical changes made to the device setup.
It's not just details of the homeowner that are collected. The video and audio recording is usually only triggered by movement or sound, but depending on their detection distances, the recording mechanism can be triggered by people walking along the street or pick up conversations of folk passing by.
Smark Locks
Smart locks are a completely keyless locking system that communicates with a property owner's smartphone or similar device over the network. They can collect a whole ream of personal data such as name, address, email address, and phone number, as well as the precise location of the lock. It will also collect cookies and usage data.
The usage data can include the following:
These details are pretty standard, pretty much all websites collect such digital fingerprinting data anyway, but in our research, we came across one brand, All Smart Locks, whose data collection is in a league of its own.
In their Privacy Policy, All Smart Locks describes “Other Data” that they “may collect” and it's quite shocking...
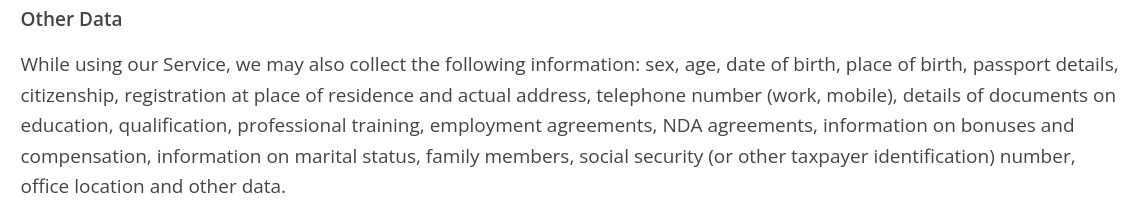 Image source: screenshot from All Smart Locks
Image source: screenshot from All Smart Locks
Smart assistant
Smart assistants are like little butlers in your home. The voice-activated devices can be asked to play music, read a book, tell us the weather forecast, control connected electronic devices, make phone calls, send messages, check our bank balance, and do an array of other tasks.
But the fact that they are voice-activated means that they are always listening. And so might be the employees of the device manufacturer... It's been reported that Amazon staff listen to Alexa recordings. You can manually turn this function off but that kind of defeats the purpose of their design.
Reviews.org compared the five most popular smart assistants in terms of the data that they collect. Amazon's Alexa was the most data-hungry, collecting 37 out of 48 possible data points.
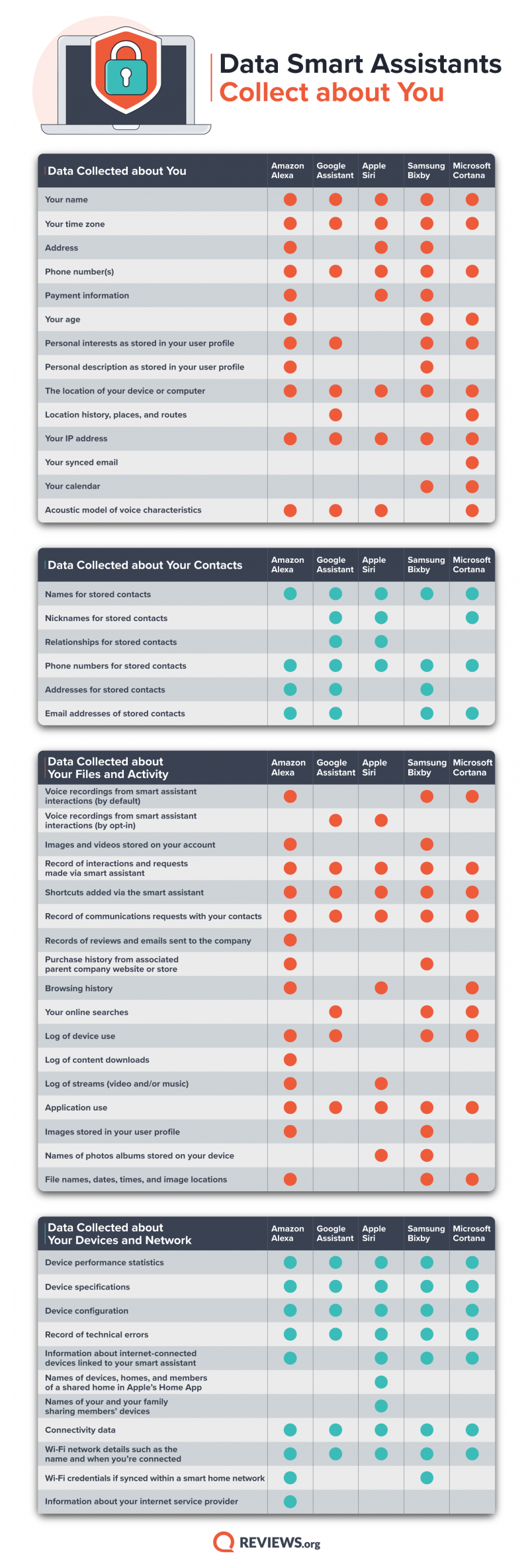 Image source: Reviews.org
Image source: Reviews.org
Sleep monitoring devices calculate the quality of sleep by tracking body movement and breathing, as well as details about the sleeping environment. This will include details on the temperature of the room, the humidity, and if there are any light disturbances.
The device will also collect data on how you use it. For example, it will know if the device is plugged in, how often you open the app, what pages you go to most often on the app, and what features you use.
Wearable fitness trackers
Wearable fitness trackers by design collect a lot of data— it's part of their selling point. The data collected may differ depending on the brand, but generally, they record your age, height, weight, gender, steps taken, distance traveled, calories burned, weight, heart rate, sleep stages, and location.
Some fitness trackers include a period tracking feature which collects a whole other set of data on menstruation, fertility, moods, sexual activity, and more.
If you visit the tracker's website, it will also collect your IP address and cookies, and if you connect your wearable device account to your social media accounts, then they will have even more information. This can include your name, profile picture, age range, language, email address, plus your friend or contact list.
Examples of Internet of Things privacy and security failures
Despite the convenience and benefits of IoT technology, many devices have been found to leak sensitive information, violating user privacy and leaving them vulnerable to a range of security risks. The vast amount of data generated by IoT devices and the lack of suitable security protocols create vulnerabilities for hackers to exploit. There is also the risk of eavesdropping by manufacturers, their employees, or unauthorized outsiders, ie. hackers.
Let's take a look at some real-world Internet of Things privacy failures.
Roomba records woman on the toilet
The MIT Technology Review reported a story about an iRobot Roomba vacuum cleaner that was found to have taken intimate images of a woman while she was using the toilet. The images were taken by a development version of the cleaning robot and sent to a third-party company called Scale AI. The company was responsible for contracting workers to categorize the data which was used to train the algorithms of the robot vacuum. However, the contractors shared some of these images to Facebook and Discord groups.
Wyze, smart device vendor data breach
Wyze, a smart home device company, suffered a massive data breach in December 2019 that exposed the personal information of 2.4 million users for a period of up to 3 weeks. Users' email addresses, health data including weight and gender, camera and WiFi names, and information on users' Wyze devices were all exposed.
Some of the data leaked was especially worrying as it had the potential for real-world harm. For example, people often name a camera after its specific location— a camera in a child's room might be called “Ben's Room”. Such specific information could have been useful to anyone planning to enter a home for malicious purposes.
IoT management platform database open and exposed
A team of “hacktivist” security researchers discovered that an Internet of Things management platform database was left open and exposed to the internet without password protection. The database was run by a Chinese company, Orvibo, and contained over 2 billion logs, including details for users in China, Japan, Thailand, Mexico, France, Australia, Brazil, the United Kingdom, and the U.S.
The logs included everything from user email addresses to passwords, IP addresses, reset codes, and smart camera recorded conversations. As well as the data, the incident also affected Orvibo's own smart home devices, which include locks, cameras, and automation kits.
Hacked Nest
A couple in Illinois has reported that a hacker spoke to their baby through one of their Nest security cameras and later hurled obscenities at them, and also altered their thermostat. The couple disconnected their cameras and contacted Nest and the police. Nest's parent company, Google, has stated that the incidents occurred due to customers using compromised passwords from other websites. The company has urged users to implement two-factor authentication and is introducing features to reject compromised passwords and allow customers to monitor access to their accounts.
Smart lock failures
In the UK, security researchers from the NCC Group identified 11 vulnerabilities in the Nuki Smart Locks that left them vulnerable to a variety of attacks. The vulnerabilities discovered could allow attackers to cause a denial-of-service attack, open doors without the owner's knowledge, intercept network traffic, and execute arbitrary code on the device.
Sextech devices hacked
Sextech is a significant segment in the IoT industry helped along by the social distancing of Covid-19. It's estimated that the number of sextech devices in use will reach 118 million by 2025. By their nature, these devices can collect not just personal data, but intimate. In 2018, a connected sex toy database was hacked leaking sensitive customer data including sexual orientation, explicit images, chat logs, email addresses, and passwords, all in clear text. Not only was this a massive violation of privacy, but the hackers could also remotely control the devices without the user's consent.
How to ensure your own Internet of Things privacy
By 2025, the amount of data generated by IoT devices is expected to reach 73.1 ZB (zettabytes). That's 422% more than the data output in 2019. With more devices, comes more data, and more potential for Internet of Things privacy failures.
So, what can you do to protect your privacy? You could stop using IoT devices and do things the old-school way. But if you love a gadget or just love the convenience that IoT devices provide, then here are a few tips you can follow.
Good password hygiene
It can't be said enough...you need to keep your passwords “healthy”. That means creating unique passwords of at least 12 characters that are a combination of lower and upper case, symbols, and digits. Don't reuse passwords, and change them regularly, every 30-90 days. All it takes is just one compromised password to open a window to your IoT devices, your network, and all of the personal or business data connected to it. If you have trouble remembering passwords, you could use a password manager.
Configure devices to your needs
When you first add a new IoT device to your network, go through the device settings to configure it to your needs. Disable any features that you don't intend on using as this can close any potential gaps.
Update your devices
Keep IoT devices up-to-date with the latest updates. Updates are more than just adding new features or a slicker user interface, they can also include security patches to fix vulnerabilities. By accepting them, you'll help keep your devices protected against the latest threats.
Limit IoT device use
Do you really need every new gadget there is? The more IoT devices you're connected to, the more potential windows into your personal and private life. It's much better to limit yourself to using devices that are absolutely necessary. If it doesn't add a benefit to your life or your business, then the privacy risks are not worth it.
Read the privacy policies
Sure, it may be dull and you just want to get to use a new gadget, but not all IoT privacy policies are the same. Some IoT device providers, (we're looking at you All Smart Locks!), collect an insane amount of data that is completely unnecessary for the functionality of the device. The idea that a door lock needs your passport number is beyond ridiculous!
With the popularity of IoT devices, you're not limited to one brand. Shop around for a company that isn't going to scrape every single last piece of data on you.
Summing up the Internet of Things privacy
The Internet of Things has undoubtedly brought about numerous benefits to our daily lives, from convenience to improved healthcare and more efficient cities. However, with the increasing number of connected devices, Internet of Things privacy and security concerns continue to grow. As users, it is crucial to be aware of the potential risks associated with these devices and take necessary precautions to protect our personal information. By staying informed and adopting best practices for privacy and security, we can continue to enjoy our connected gadgets without compromising our safety and privacy.
Read more: 5 Major Problems With Facial Recognition Technology
Ruby is a full-time writer covering everything from tech innovations to SaaS, Web 3, and blockchain technology. She is now turning her virtual pen to the world of data privacy and online anonymity.

Chapter 14: IoT Hacks

Dive into the unsettling world of government-controlled GPS tracking!

Trash Talk: How your garbage can be exploited by hackers, law enforcement, and government agencies

It’s time to uncover how government surveillance gets personal.
Discover the world's #1 privacy solution
Coming soon
Coming soon
Coming soon

